
Wednesday, December 22nd, 2010
I was very excited when the Diaspora project was announced eight months ago and its initiators raised $200,000 within just a few weeks: The ‘social web’ will become a distributed system at last! My dream of the Web 3.0 will soon come true!
Then, in September, the first preview release was published. I didn’t have the time to try it out myself, but one thing became obvious very soon: The developers had completely missed their goal to build a secure alternative to Facebook that really respects and protects its users’ privacy—the system had a whole lot of really bad security issues. In a software project that claims to be so clearly focused on security and independence from central instances, data security must actually have such a high priority right from the beginning that things like “anyone can take full control anyone else’s user account” simply never happen. Security is not something that just happens, nor is it just another feature that you can add to an existing system whenever you like.
No support
At least the developers managed to close security issues that Patrick McKenzie and others had found in the preview release before publishing the ‘consumer alpha’ version. They did not at all remove my doubts about the imminent breakthrough though. Here’s an example why:
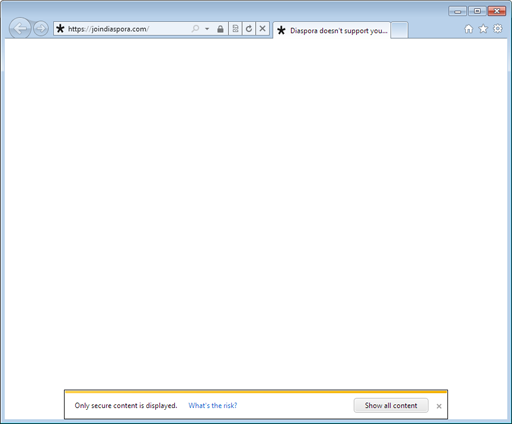
Users typing the address ‘joindiaspora.com’ into a Microsoft Internet Explorer address bar were getting a blank page with a hint saying ‘Diaspora doesn’t support you…’ at the top and another one, stating that only secure content was currently being displayed, at the bottom.
In order to understand what had happened there, one had to take a closer look and to be familiar with the basics of SSL enryption. The Diaspora software classified each page request depending on the browser used, marking Internet Explorer as ‘bad’ and (probably) anything else as ‘good’. Users of the latter were getting the actual page; Internet Explorer users were instead seeing an advertisement for Google Chrome Frame—a piece of software that can be plugged into Internet Explorer so that it basically becomes Google Chrome inside an Internet Explorer window—on a page titled “Diaspora doesn’t support your browser”, which was shortened to the somewhat unfriendly message “Diaspora doesn’t support you…” due to default browser tab width. Additionally, it seems the Diaspora developers apparently hadn’t even bothered trying it out at all—otherwise they would have noticed that the default security settings in Internet Explorer prevent non-encrypted (HTTP) content from being displayed within an encrypted (HTTPS) page (hence the blank page with the ‘secure content’ hint).
One click on the ‘Show all content’ button (or some changes in the Internet Explorer security settings) later, the user was allowed to see the Google Chrome Frame advertisement in its full glory.

Sure, one might say that Microsoft should rather have stayed out of the browser marked altogether instead of publishing eight major releases of a piece of software that gave lots of grief to web developers during the past 15 years with its weird interpretation of web standards (and made fraudsters who wanted to spread malware happy with its fundamentally broken security concept). But:
- When building a system that needs masses of users (including ‘normal’ people, not just nerds) to be successful, deliberately and unnecessarily excluding users who still use Internet Explorer (whether voluntarily, involuntarily, or because they just don’t care) is simply out of the question.
- I deliberately wrote “eight major releases” because I am not incluing version 9 which is currently in public beta. For the first time, Microsoft is in the process of releasing a really decent browser that can easily compete with Mozilla Firefox. But the Diaspora developers have obviously heard so little of the progress of the past months that they didn’t even bother restricting the Chrome Frame redirection to Internet Explorer 8 and older.
- The SSL mistake is so obvious that it needn’t be discussed further. It would have taken just one ‘s’ to make it work as intended.
No ideas
There is another aspect why I don’t really believe in Diaspora’s success. As my friend Wolfgang put it recently on Twitter, “Diaspora is like the KDE desktop: the open source imitation of a commercial product without a vision of its own.” Diaspora doesn’t do anything substantial that hasn’t already been standard functionality on Facebook, Myspace, Orkut long before. They even ignored the opportunity to apply the concept of asymmetric subscriptions—which has proven to work very well on Flickr and Twitter—to a ‘classic’ social networking platform without crippling it like Facebook did with its ‘likes’ and ‘pages’. (Michael ‘mspro’ Seemann explained a few weeks ago why this would be so essential.)